Table of Contents [expand]
Last updated January 28, 2026
This architecture shows how to peer a Heroku Private Space with an AWS VPC in order to provide a secure way of accessing resources that you may have running in your VPC, such as an Amazon Redshift cluster or AWS RDS for SQL Server instance, from apps running in the Private Space.
Scenario
- You have an AWS service (such as Amazon RDS or Amazon Redshift) running in an AWS VPC.
- You want one or more Heroku apps to interact with your AWS service over a private connection.
- You want to ensure that the connection’s traffic does not traverse the public internet.
Architecture
This reference architecture uses Private Space Peering to establish a private network connection between a Heroku Private Space and an AWS VPC:
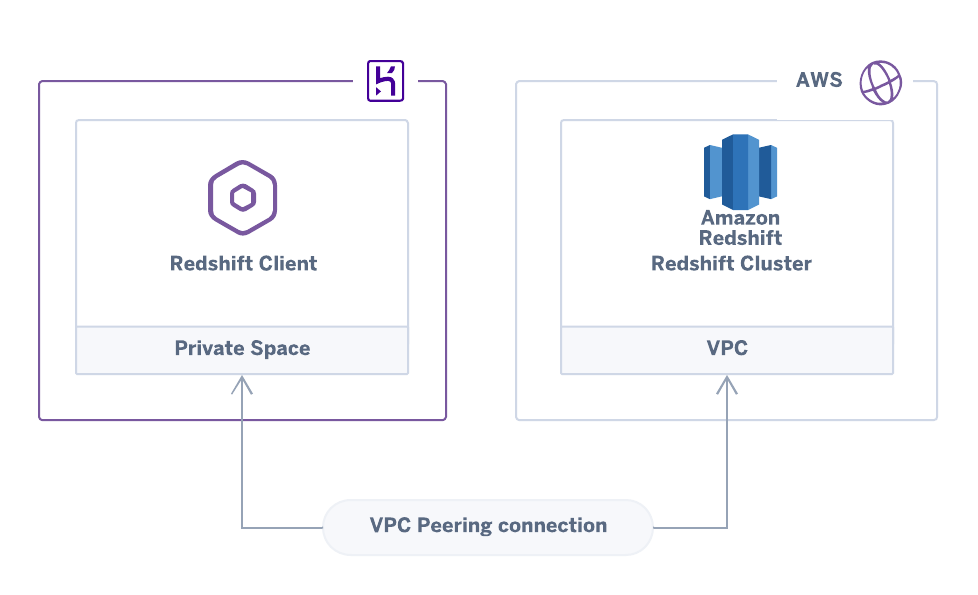 An Amazon Redshift cluster connecting to a Heroku app across a peered VPC connection
An Amazon Redshift cluster connecting to a Heroku app across a peered VPC connection
This architecture is useful if you’re running any AWS service within a VPC. For example, you might be using an Amazon Redshift cluster to analyze data, and by connecting the VPC to your Heroku application, you can securely transfer data from your Heroku Postgres database to the Redshift cluster for analysis.
As another example, you might have an existing integration that inserts data into an AWS RDS for SQL Server instance. This architecture lets you bridge your Heroku application and the SQL Server instance, providing access to the data without traversing the public internet.
Components
Required
- Your Heroku app(s) must run in a Heroku Private Space, which requires Heroku Enterprise.
- Your AWS account must have permission to make a VPC peering connection request.
Implementation Guidelines
Follow the guidelines in Private Space Peering to implement this architecture.
After you peer your Private Space with the VPC holding your AWS service, the Heroku applications within the Private Space have direct access to the service. For example, your app can establish a connection to a Redshift cluster to transfer data or initiate analyses.
Example implementation
This Terraform script provides a simple implementation of this scenario. It:
- Creates a Heroku Private Space
- Creates an Amazon VPC together with an Amazon Redshift Cluster
- Peers the Private Space and the VPC, and sets up the appropriate security groups
- Deploys a Redshift client application to Heroku that connects to the Redshift database
See Using Terraform with Heroku for details on how to use Terraform with Heroku.
Pros / Cons
Pros
- All communication can flow over a private connection.
Cons
- You need to be familiar with configuring and maintaining VPCs - in particular setting up network ACLs and routing tables.
- You need to allocate network space on your private network for the Private Space.
- If your credentials change on AWS Redshift, you will have to manually update the config vars on your Heroku apps.
Additional Reading
- Private Space Peering
- Using Terraform with Heroku
- Amazon Redshift (AWS documentation)