Last updated February 26, 2026
SSO is available only for Heroku Teams and Heroku Enterprise customers.
Heroku integrates with your existing identity provider (IdP) to enable single sign-on (SSO) using the same credentials and login experience as your other SSO-enabled service providers, such as Slack and Dropbox.
Using SSO, an employee logs into Heroku using your identity provider’s interface instead of the Heroku login page. The employee’s browser redirects to Heroku to authenticate. With SSO enabled, Heroku’s own login mechanism is disabled, meaning that authentication security shifts to your IdP, and coordinated with your other service providers.
Heroku doesn’t notify your employees when SSO is set up, changed, or deactivated for your organization. Make sure to communicate these changes.
When enabling SSO, include the Using Single Sign-on (SSO) Services with Heroku, for End Users article in your rollout communications.
Prerequisites for SSO with Heroku
- Your company’s identity provider (IdP) must support the SAML 2.0 standard.
- You must have administrative permissions on the IdP.
- You must enforce multi-factor authentication (MFA) at the IdP-level.
- You must have admin permissions on a team to enable the SSO feature.
Identity Providers with Built-in SSO support for Heroku
The following major IdPs provide built-in support for Heroku. To set up SSO for these IdPs, follow the instructions on the vendor’s site.
To set up SSO with Microsoft Active Directory, use the SAML 2.0 instructions below.
SSO Setup for Other SAML 2.0-Compliant IdPs
Most SAML 2.0-compliant identity providers require the same information about a service provider to set up SSO. In the case of Heroku, relevant values are available in the Settings tab of the Heroku Team you want to enable SSO for:
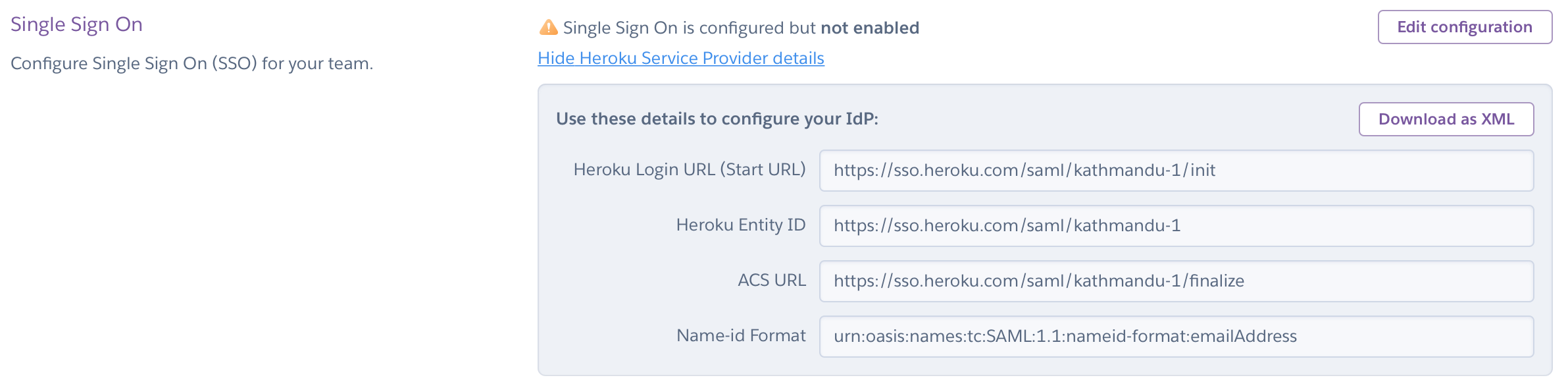
You must have admin permissions on a team to see this information and to enable SSO.
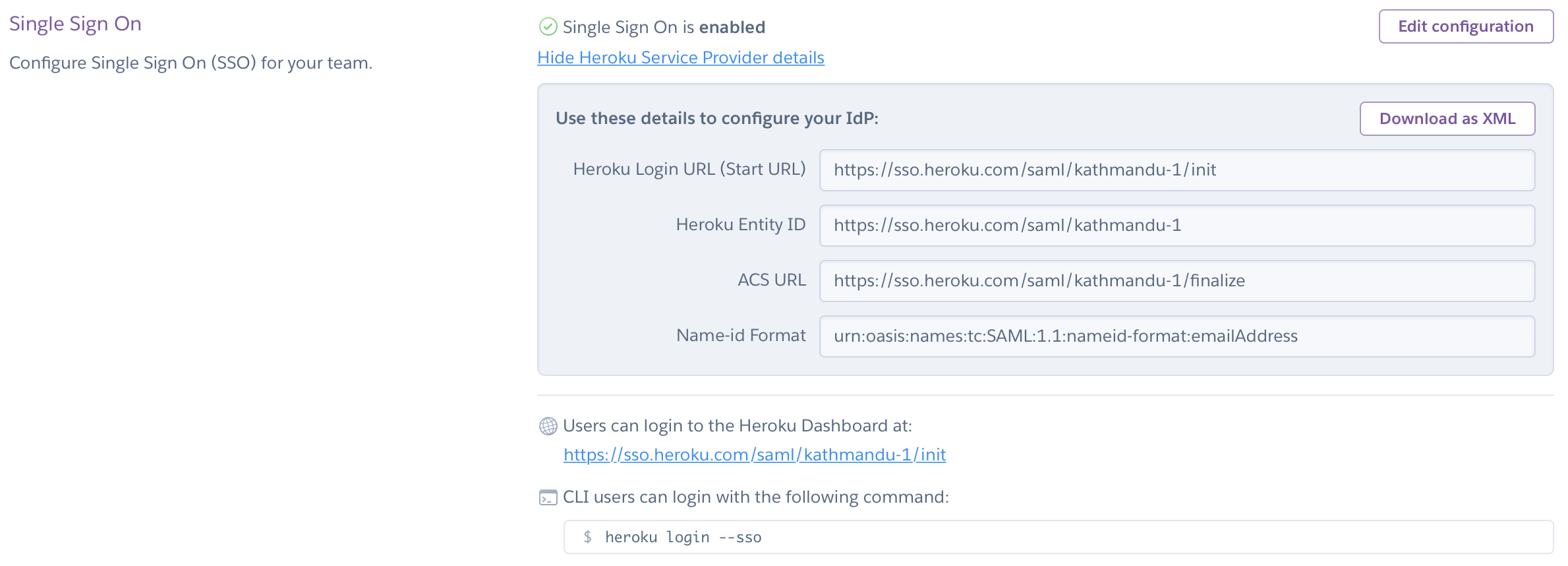
After configuring SSO on your IdP, you can upload or enter metadata manually. When setup is successful, administrators see a confirmation dialog, and the URL of the SSO login for end users displays. Share this URL with your organization.
Providing Multiple IdP Certificates
To enable zero downtime with SSO certificate changes, you can add up to three SSO certificates for teams. We accept SAML assertions signed under any of the non-expired SSO certificates, making it possible to seamlessly switch to a new identity provider certificate without downtime.
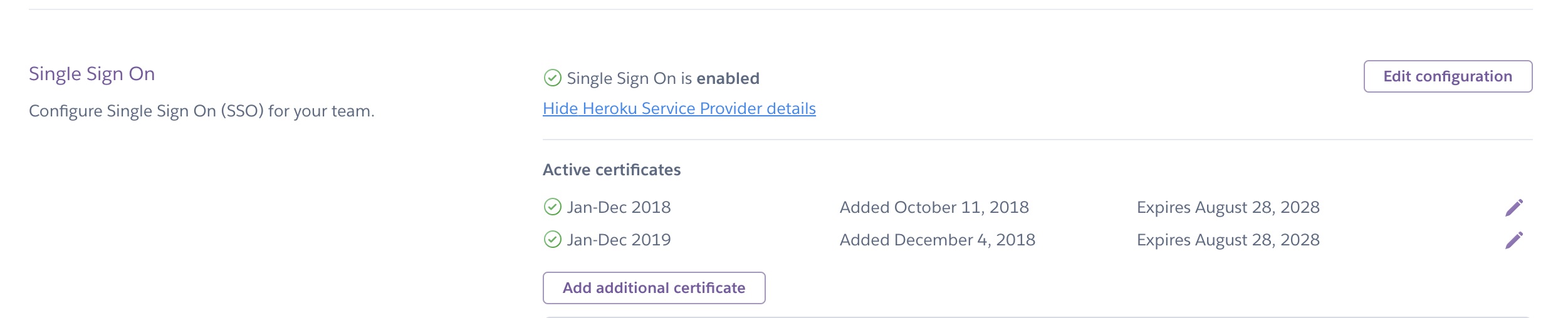
Heroku also sends email notifications to users with the admin permissions of an SSO-enabled team at 30 days, 7 days, and one day before a certificate expires. This notification gives admins a chance to update expiring certificates and avoid user lockout.
For improved security, configure your IdP to sign both SAML response and assertion using SHA-256 if the IdP supports it.
End-User Account Creation and Removal
Creating End-User Accounts
To add end users, create accounts for those users in your IdP. The first time a user logs in to Heroku via the IdP, a Heroku account gets created via automatic IdP provisioning. The user’s access to the team’s resources and settings depends on the default role to assign new users, as specified by an admin in the team’s Settings tab:
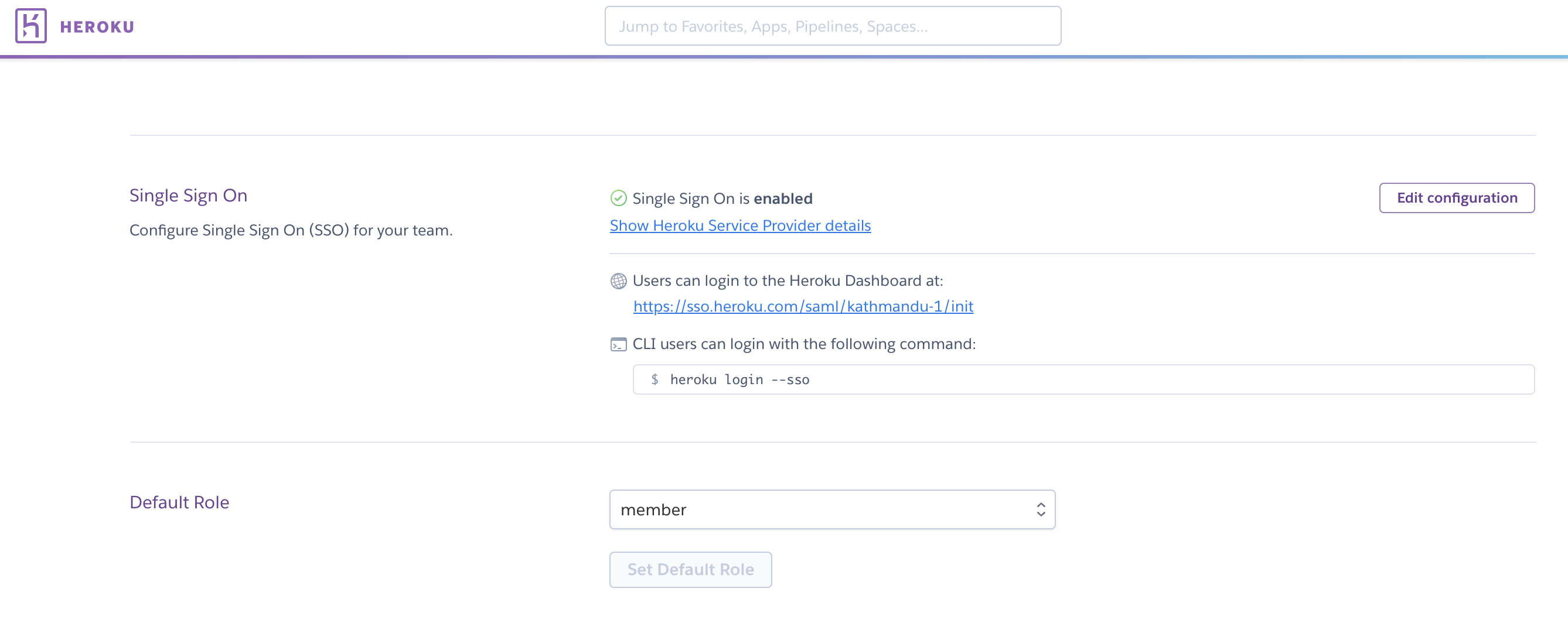
The default role for new users is member unless the admin changes this setting.
After the account provisions, the end user receives a verification email and must click the included acknowledgment link.
Create an admin user account directly with Heroku, not via the IdP, so you can still access Heroku if the IdP isn’t working properly.
Create an integrations user account directly with Heroku, not through the IdP, in case you need to set up integrations that require a Heroku API key.
Removing End-User Accounts
Removing an end user from your IdP prevents the user from logging in to their corresponding Heroku account, but it doesn’t remove the account from Heroku. To ensure against possible API access to team resources before API keys time out, remove the end user’s account from the team associated with the IdP.
To remove an end-user account from Heroku that was created via automatic IdP provisioning, the Identity Administrator can contact Heroku Support.